Cybersecurity in Mining – Thematic Research
Powered by ![]()
All the vital news, analysis, and commentary curated by our industry experts.
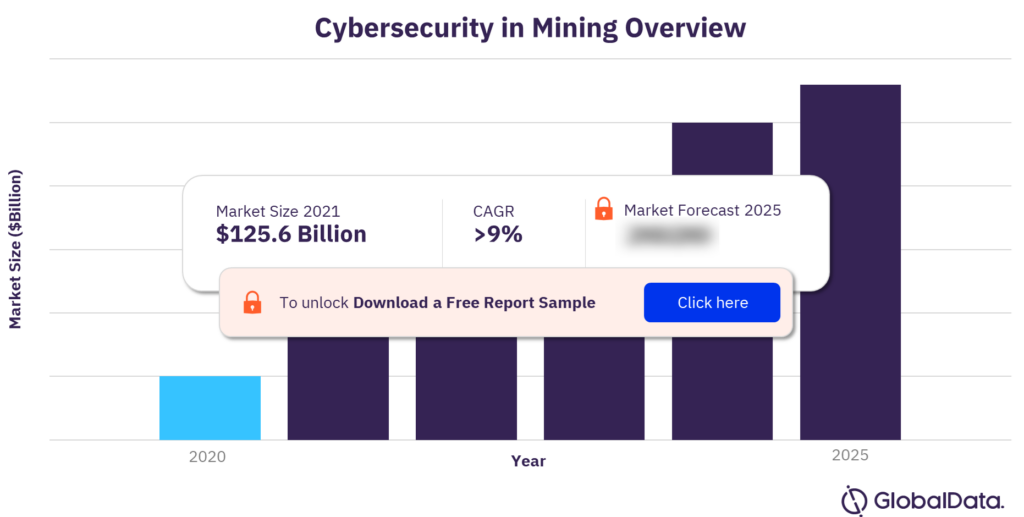
The global cybersecurity market size was $125.6 billion in 2020. The market is projected to grow at a CAGR of 9% during the period 2020-2025. Cybersecurity is the practice of defending computers, servers, mobile devices, electronic systems, networks, and data from malicious attacks. The IoT sensors, augmented reality (AR) devices, autonomous vehicles, and drones that improve mining operations are equally capable of halting activity if they fall prey to cyberattacks. The operational technology (OT) networks of mining operations are particularly vulnerable to cyberattacks due to their lower security maturity than corporate networks.
Cybersecurity in mining overview
For more insights on this report, download a free report sample
What are the key value chains in cybersecurity in mining industry?
The key value chain in cybersecurity in mining industry are cybersecurity hardware, cybersecurity software, and cybersecurity services.
Cybersecurity Hardware
With chips now being used in mission-critical servers and safety-critical applications, protecting chips from cyberattacks is becoming more critical and more expensive. Systems vendors such as Apple and Amazon are increasingly designing their own chips rather than buying commercially developed devices and intellectual property (IP) created by third-party developers. These vendors are developing their own ecosystems and requirements, and security is a key concern.
Cybersecurity Software
The software element of our cybersecurity value chain comprises the following areas: identity management, network security, endpoint security, threat detection and response, cloud security, data security, email security, application security, unified threat management, and vulnerability management.
Cybersecurity Services
The services element of the cybersecurity value chain comprises the following areas: managed security services, post-breach response services, and risk and compliance services. Services are typically outsourced because of the complexity of addressing cybersecurity-related issues, such as staying on top of vulnerabilities, identifying and responding to threats, and meeting compliance requirements.
Who are the key cybersecurity adopters in the mining industry?
The key cybersecurity adopters in the mining industry are Anglo American, Antofagasta, BHP, Nippon Steel, and Rio Tinto.
Who are the key cybersecurity vendors in the mining industry?
The key cybersecurity vendors in the mining industry are Accenture, Alphabet, Check Point Software, Cisco, Cloudflare, CrowdStrike, Darktrace, Dell Technologies, Fortinet, and IBM.
Who are the key specialist cybersecurity vendors in the mining industry?
The key specialist cybersecurity vendors in the mining industry are ABB, Dragos, Malwarebytes, and Nozomi Networks.
Market report scope
| Market size (Year – 2020) | $125.6 billion |
| CAGR | >9% |
| Forecast period | 2020-2025 |
| Key value chains | Cybersecurity Hardware, Cybersecurity Software, and Cybersecurity Services |
| Key adopters | Anglo American, Antofagasta, BHP, Nippon Steel, and Rio Tinto |
| Leading vendors | Accenture, Alphabet, Check Point Software, Cisco, Cloudflare, CrowdStrike, Darktrace, Dell Technologies, Fortinet, and IBM |
| Key specialist vendors | ABB, Dragos, Malwarebytes, and Nozomi Networks |
This report provides:
- An overview of the cybersecurity value chain, case studies of cybersecurity deployments in mining, market size and growth forecasts, specialist cybersecurity vendors for mining companies, and analysis of the mining companies leading in cybersecurity adoption.
- A detailed value chain comprising the 14 segments of cybersecurity (including hardware, software, and services), with leading and specialist vendors, and leading mining adopters identified across all segments.
- Industry analysis, including forecasts and cybersecurity revenues to 2025, alongside sector-specific analysis using GlobalData’s deals, patents analytics, company filing, and hiring trends.
- An overview of M&A deals driven by the cybersecurity theme and a timeline highlighting milestones in the development of cybersecurity.
- Analysis of the leading adopters in mining, their key moves in the theme, and their position in our thematic scorecards.
- Breakdown of the key challenges in the mining industry, and how cybersecurity technologies can help to solve those challenges, including digitalization, productivity, and ESG.
Reasons to Buy
- Position yourself for success by understanding the ways in which cybersecurity can help to solve the major challenges for the mining industry, such as those of digitalization, ESG, and COVID-19.
- Identify the leading, and specialist vendors of cybersecurity solutions for the mining industry. Discover what each vendor offers, and who some of their existing clients are.
- Quickly identify attractive investment targets in the mining industry by understanding which companies are most likely to be winners in the future based on our thematic scorecard.
- Gain a competitive advantage in the mining industry over your competitors by understanding the potential of cybersecurity solutions in the future.
ABB
Accenture
Acronis
Airbus (Stormshield)
Akamai
Alert Logic
Alibaba
Alphabet (Google)
Alphabet (Siemplify)
Amazon
AMD
Analog Devices
Anglo American
AngloGold Ashanti
Antofagasta
AnyVision
Appgate
Apple
Applied Risk
Aqua Security
Arcon
AT&T
Atos
Attivo Networks
Aveva
Aware
BAE Systems
Baidu
Barracuda
Barracuda Networks
BeyondTrust
BHP
BioEnable
Blackberry
BMC Helix
Boliden
Broadcom
BT
Cadence Design Systems
Capgemini
Cato
Check Point Software
Checkmarx
China Telecom
China Unicom
CipherCloud
Cisco
Claroty
Clear Secure
Clearview
Cloudcheckr
Cloudera
Cloudflare
CloudPassage
CMITech
Code42
Cognitec
Cognizant
Contrast Security
CrowdStrike
CyberArk
Cyberbit
Cybereason
Cynet
D3 Security
Darktrace
Dashlane
Delinea
Dell Technologies
Deutsche Telekom
Dragos
Duo Security
DXC Technology
ekey
Equifax
Ermetic
Exabeam
Expanse
Extreme
EY
Eyelock
F5 Networks
FireEye
First Quantum Minerals
Forcepoint
Forescout
ForgeRock
Fortescue Metals
Fortinet
Foxpass
Fugue
Fujitsu
GitLab
HCL Technologies
Helpsystems
Herjavec Group
HID Global
Hitachi
Horizon Robotics
HPE
Huawei
IBM
IBM (Red Hat)
Idemia
iFlytek
Illumio
Ilumio
Impulse
Informatica
Infosys
Innovatrics
Intel
Invicti
iProov
Iris ID
IriusRisk
Ironscales
Ivanti
Ivanti (MobileIron)
Juniper Networks
Kairos
Kaspersky Labs
KnowBe4
KPMG
KT
Lacework
LastPass
Lockheed Martin
LogMeIn
LogMeOnce
Logrhythm
Lookout
Lumen Technologies
Malwarebytes
ManageEngine
Marsh
Marvell
Megvii
Mentor Graphics
Micro Focus
Micron Semiconductor
Microsoft
Mimecast
NCC
Netskope
Nippon Steel
Nokia
NordPass
Nornickel
Northrop Grumman
Nozomi Networks
NTT Data
NXP Semiconductors
NXT-ID
Okta
Okta
Onapsis
One Identity
OneLogIn
OneSpan
OneTrust
Oracle
Orange
Orca Security
Palantir
Palo Alto Networks
Perimeter 81
Ping Identity
Portnox
Proofpoint
PwC
Qualys
Rapid7
Raytheon BBN
Raytheon Technologies
RedSeal
Renesas
Resolver
Rio Tinto
RSA
Ruckus
SAIC
SailPoint Technologies
Samsung Electronics
SecureAuth
SecureOne
Secureworks
Securonix
SenseTime
SentinelOne
Singtel (Trustwave)
Skybox Security
Skyhigh Security
Snyk
Softbank (Arm)
SonicWall
Sophos
South32
Splunk
STMicroelectronics
Sumo Logic
Swimlane
Synopsys
Tanium
Tata Consultancy Services
Tata Steel
Tech Mahindra
Tech5
Teck Resources
Telstra
Tenable
Tessian
Thales
ThreatConnect
Threatmetrix
Threatmodeler
TitanHQ
Trellix
Trellix
Trend Micro
TrueFace.AI
Untangle
Vedanta
Veracode
Verizon
Versa
VMware
VMware
WatchGuard
Waterfall
WhiteHat Security
Wipro
Yubico
and Zscaler.
Table of Contents
Frequently asked questions
-
What was the global cybersecurity revenue in 2020?
The global cybersecurity revenue was valued at $125.6 billion in 2020.
-
What is the global cybersecurity growth rate?
The global cybersecurity market is projected to grow at a CAGR of 9% during the period 2020-2025.
-
What are the key value chains in cybersecurity in mining industry?
The key value chain in cybersecurity in mining industry are cybersecurity hardware, cybersecurity software, and cybersecurity services.
-
Who are the key cybersecurity adopters in the mining industry?
The key cybersecurity adopters in the mining industry are Anglo American, Antofagasta, BHP, Nippon Steel, and Rio Tinto.
-
Who are the key cybersecurity vendors in the mining industry?
The key cybersecurity vendors in the mining industry are Accenture, Alphabet, Check Point Software, Cisco, Cloudflare, CrowdStrike, Darktrace, Dell Technologies, Fortinet, and IBM.
-
Who are the key specialist cybersecurity vendors in the mining industry?
The key specialist cybersecurity vendors in the mining industry are ABB, Dragos, Malwarebytes, and Nozomi Networks.
Get in touch to find out about multi-purchase discounts
reportstore@globaldata.com
Tel +44 20 7947 2745
Every customer’s requirement is unique. With over 220,000 construction projects tracked, we can create a tailored dataset for you based on the types of projects you are looking for. Please get in touch with your specific requirements and we can send you a quote.